Hardware Hacking Tp Link
Feb. 16, 2023Background
Many IoT devices today use a serial communication interface known as the Univeral Asynchronous Receiver Transmitter (UART). The purpose of this interface is to give direct access to the IoT operating system via a command line interface (CLI) for debugging. In many cases, the underlying operating system is just a Unix system, which means backdooring these systems should be (hopefully) very simple.
I worked on this a while ago but finally was able to get all of the images together and uploaded. I found an unused TP-Link router and thought I’d mess with it a little. I noticed it had a UART connection which gave me an easy root shell. Then I modded the firmware and flashed it onto the device. It was easy enough… But I may have soft locked it :P
Recon
Here is the device in question:

TP-Link Technologies Co., Ltd. 300Mbps Wireless N Router WR841NV14
FCCID: TE7WR841NV14
I threw the ID into fccid.io and found its documentation along with internal photographs:
I took mine apart and found that the internals were pretty much the same (obviously):
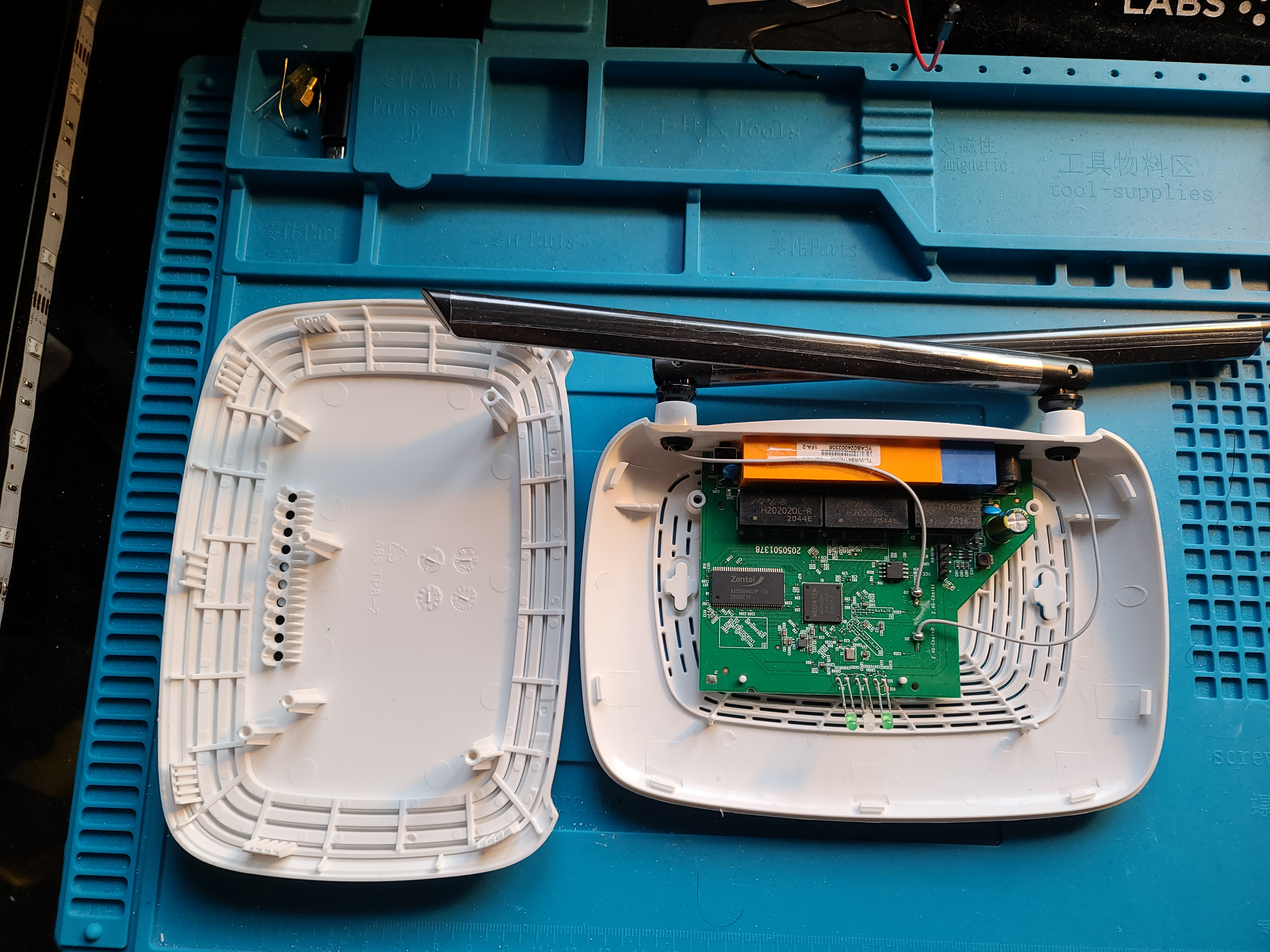
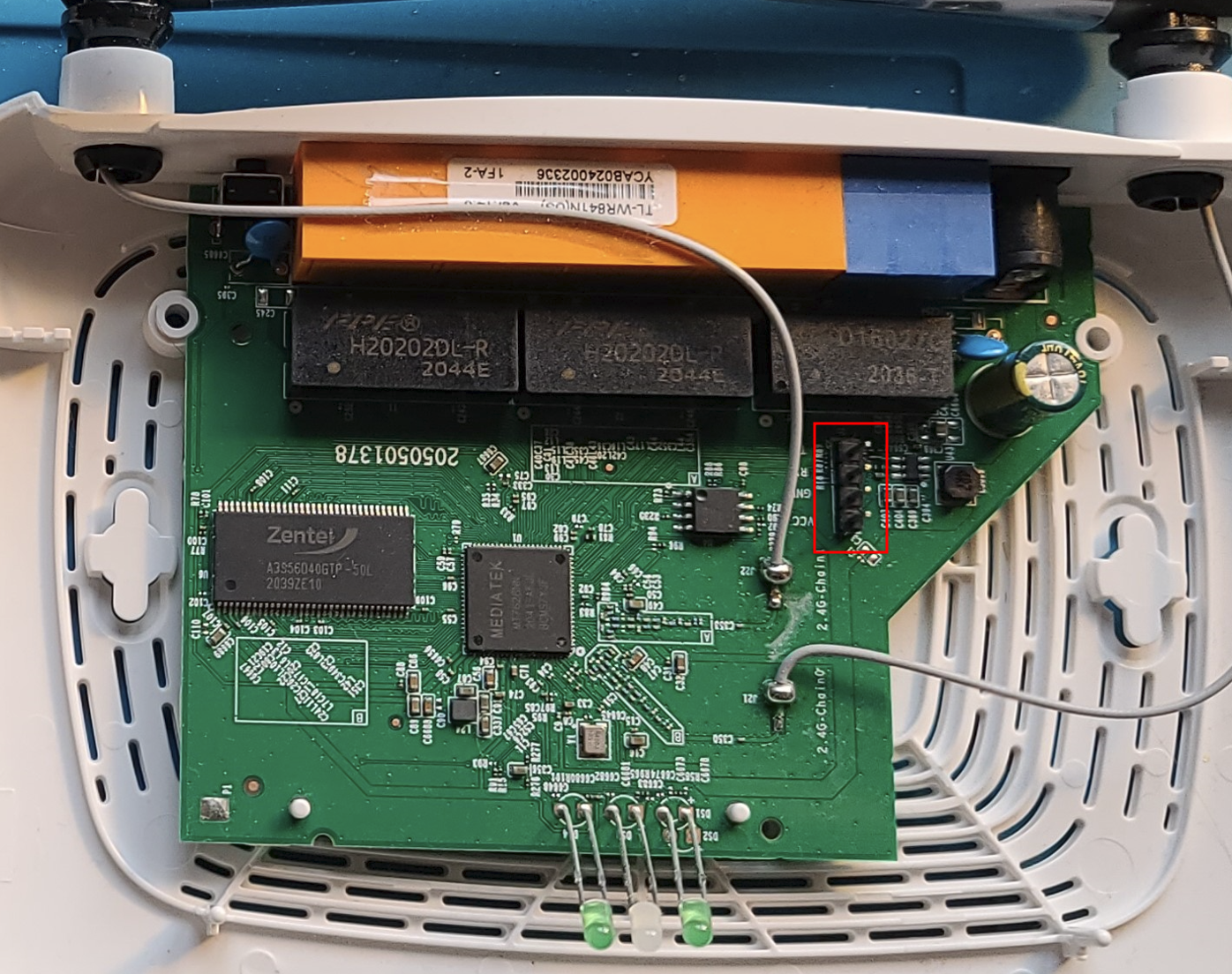
Then I looked around at the various chips and discovered a row of 4 pins which looks to be a UART connection interface! (I soldered on the header pins after I found it)
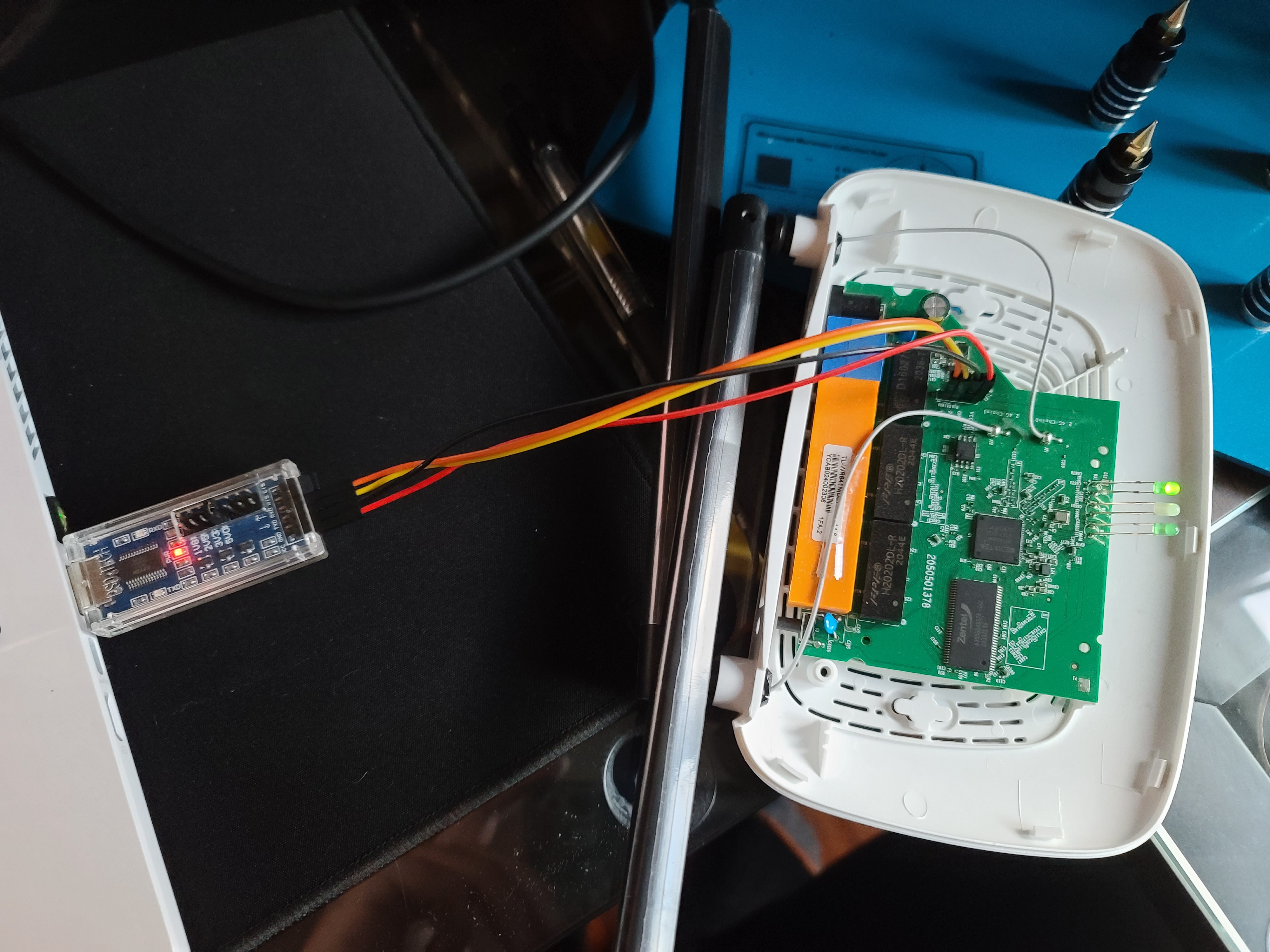
I grabbed my UART to USB interface adapter and plugged in everything:
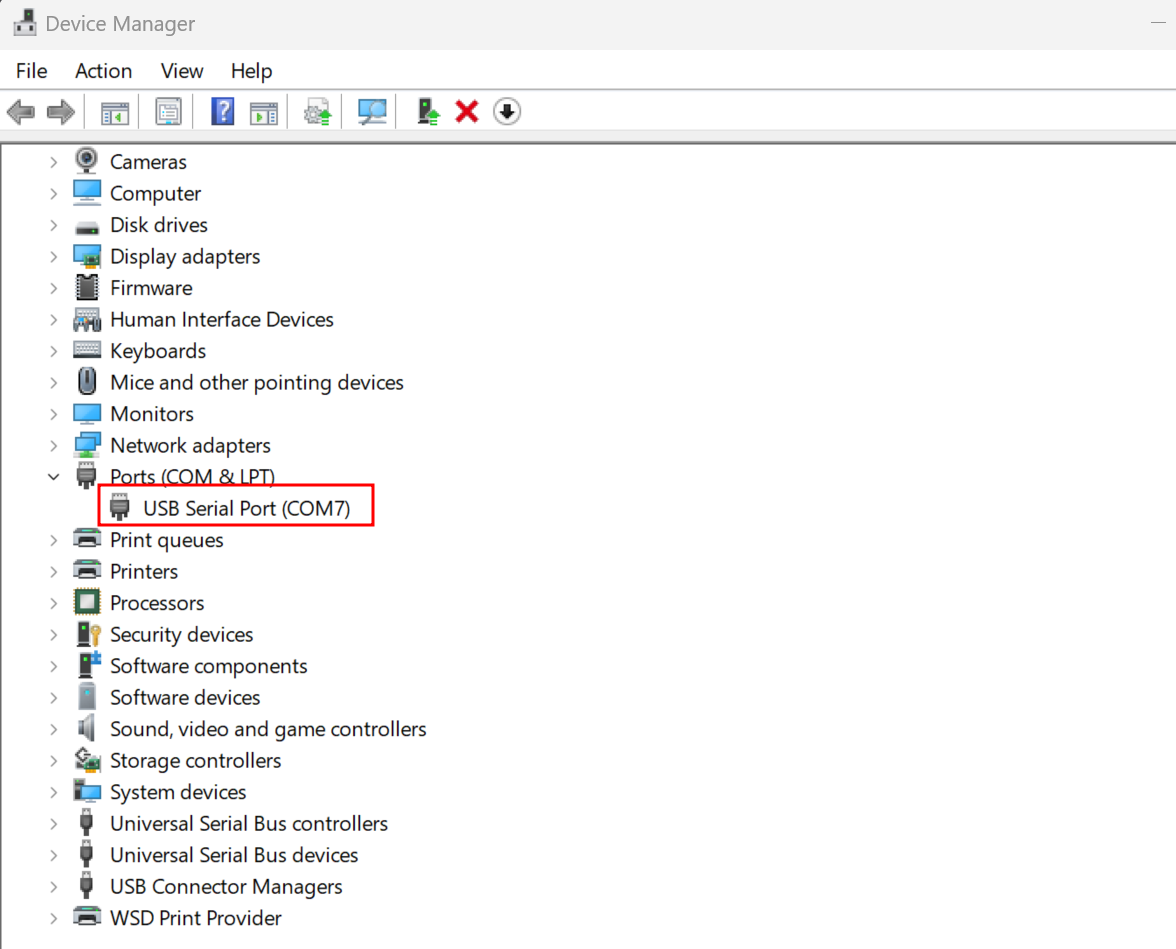
Then I opened up PuTTY and connected to COM7 which was the serial device that appeared in the Windows Device Manager:
I set the baud rate to 115200 because the device was relatively new and I figured it would be a good first starting guess. And I was right!
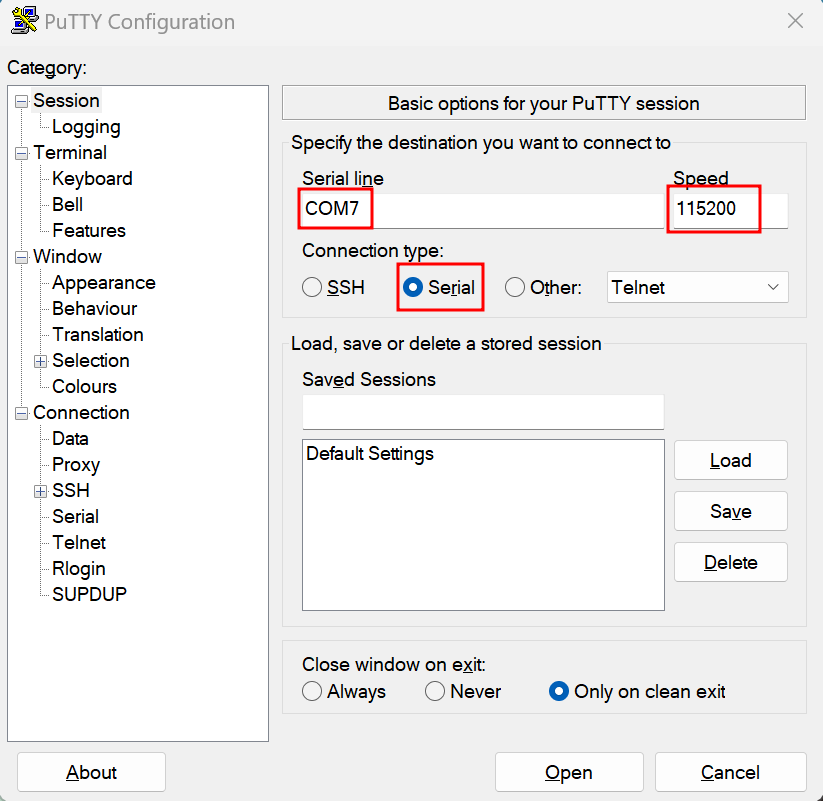
And just like that I had a root shell on the router.
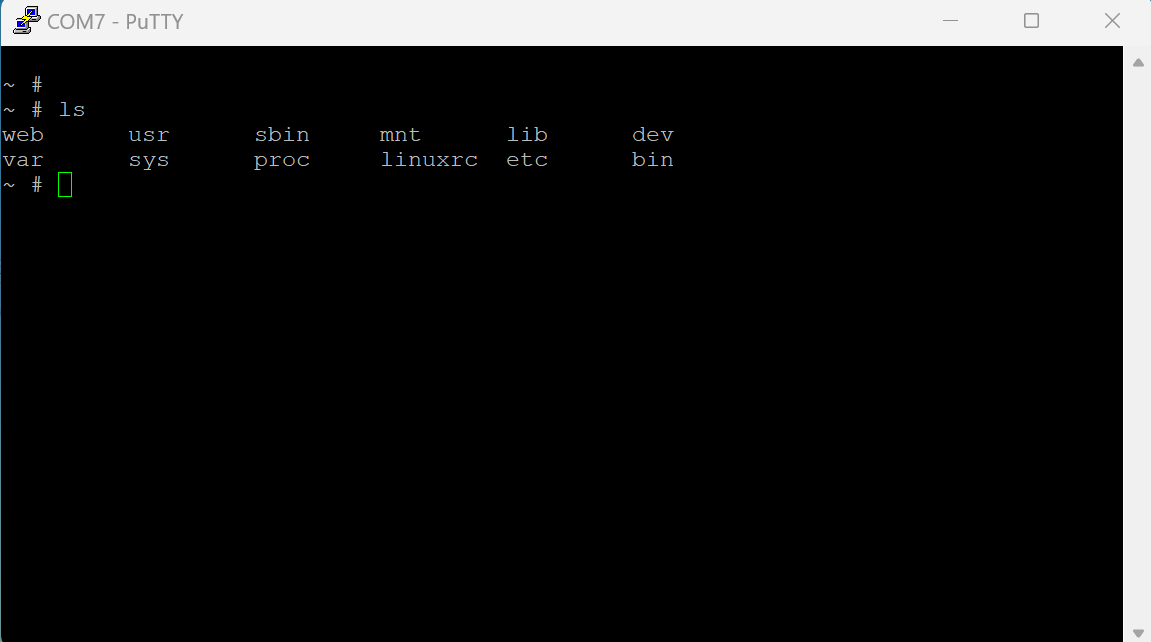
Pilfering
After gaining access like a total 1337 h4x0r I took a look at /etc/passwd
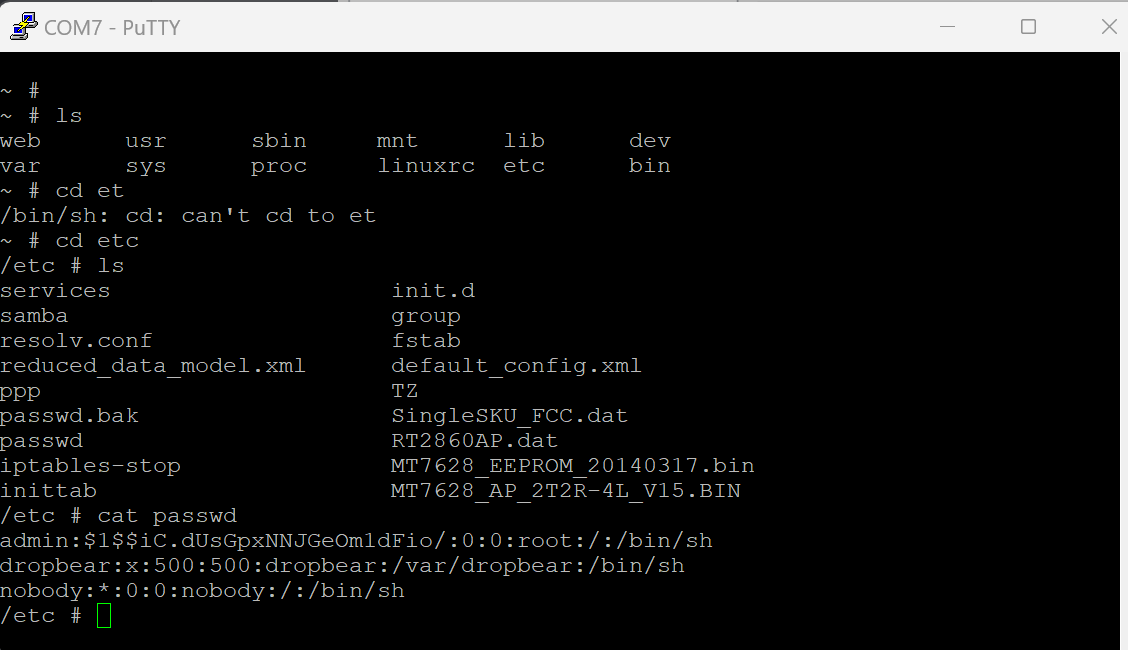
This made it easy enough to throw into hashcat and I came across a pretty funny result:
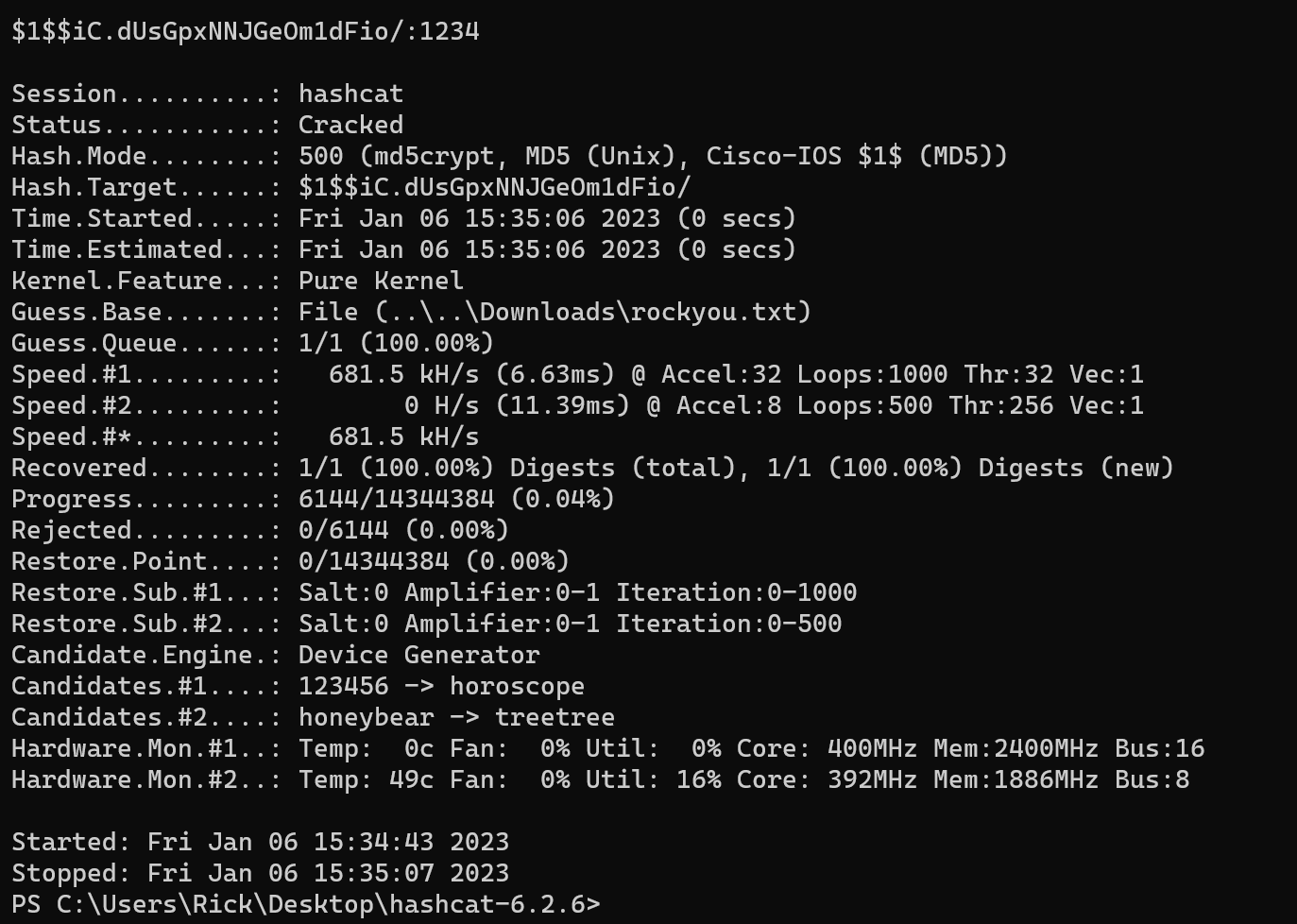
This will give us SSH access to the router with the user admin, and based off of the running processes, ssh an active service:
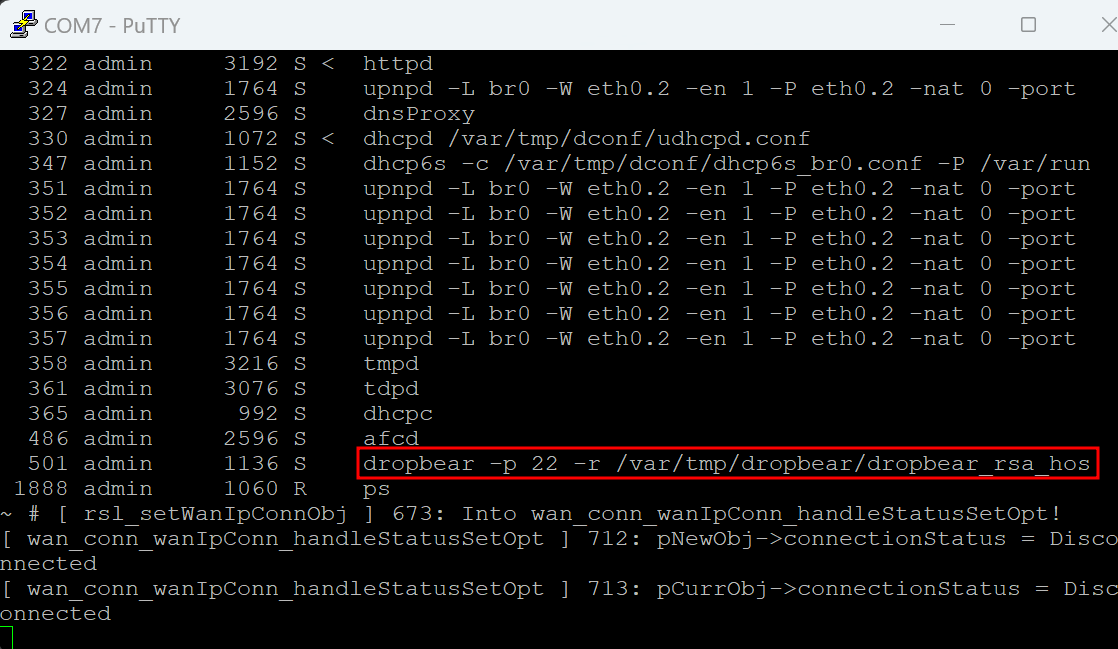
Modding the Firmware
I wanted to install some sort of backdoor but the filesystem is read-only. So I had to resort to modding the firmware and reflashing it.
I went to the TP-Link site and downloaded their latest firmware image
I downloaded it, unzipped it, and then used firmware-mod-kit to extract it. I could have just use binwalk to extract, but doing it this way allowed me to repack it with relative ease.
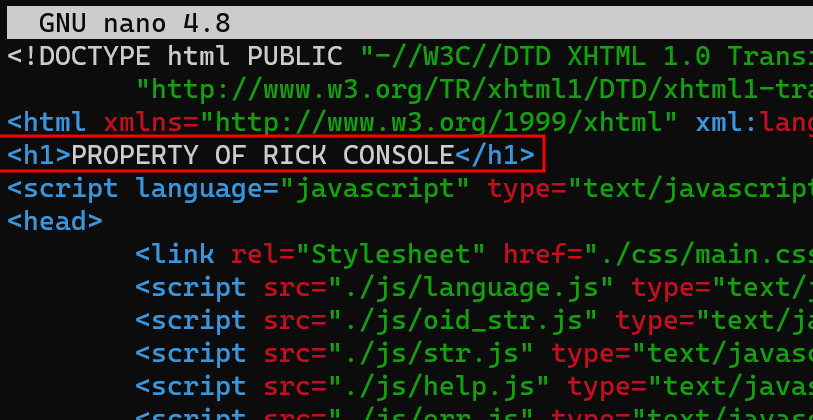
After making a seemingly minor addition to one of the web files and repacking the firmware, I flashed it onto my device.
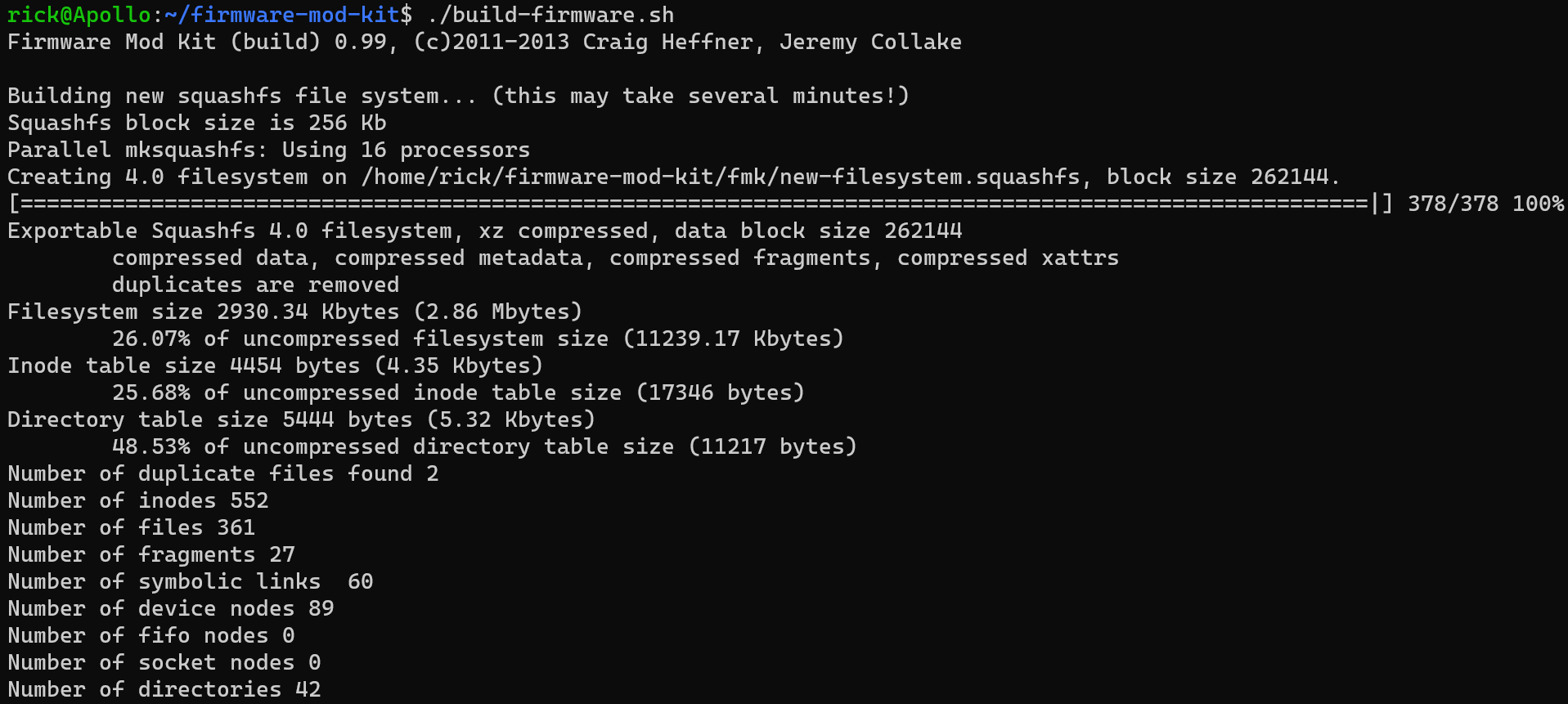
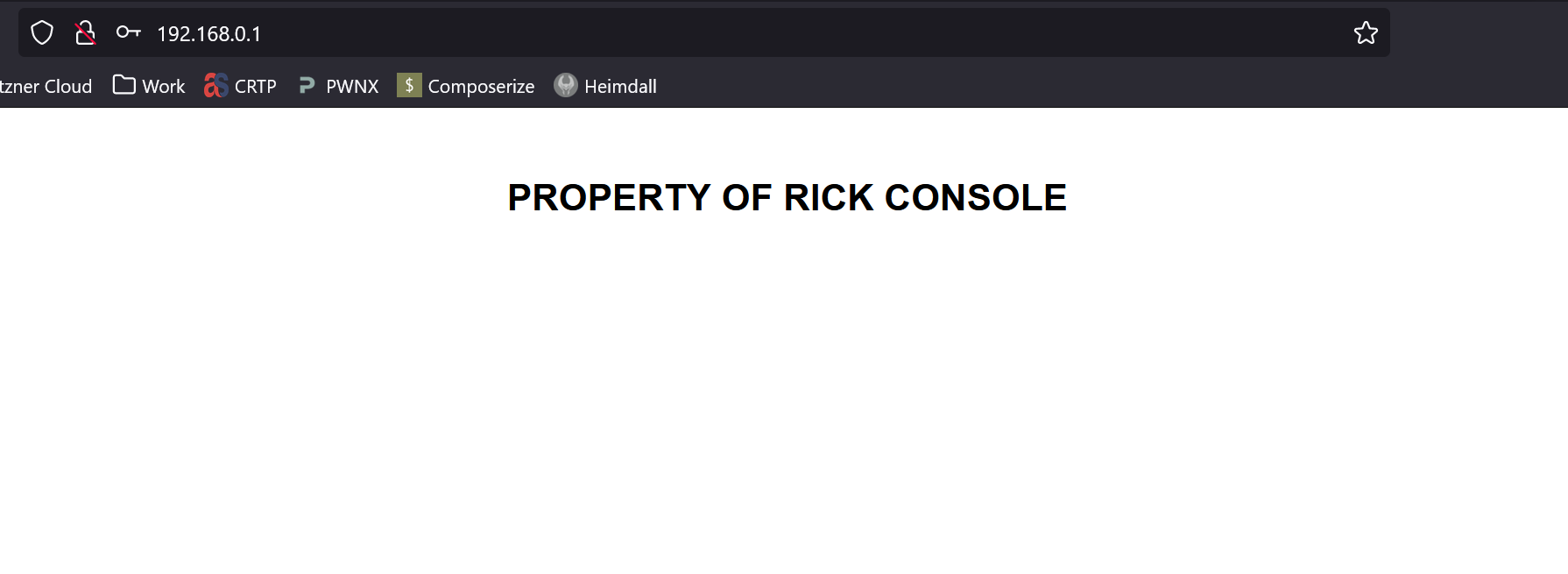
After the router rebooted, I traveled to its IP address and found that my changes were applied successfully! However, the page it now broken and I cannot access any of the routers functions. Sloppy front end development on my part. Hopefully I can fix it soon.
Conclusion
Being able to identify certain aspects of SBCs can be very valuable for hardware hacking! This was a great experiment in firmware modding and the UART interface.